How to Use the TPM: A Guide to Hardware-Based Endpoint Security. The TPM, a secure cryptographic integrated circuit (IC), provides a hardware-based approach to manage user authentication, network access, data protection and. The Future of Customer Care does a tpm handle all cryptography and related matters.
How to Use the TPM: A Guide to Hardware-Based Endpoint Security
Using TPM 2.0 As a Secure Keystore on your Laptop - TIB AV-Portal
How to Use the TPM: A Guide to Hardware-Based Endpoint Security. Best Solutions for Remote Work does a tpm handle all cryptography and related matters.. The TPM, a secure cryptographic integrated circuit (IC), provides a hardware-based approach to manage user authentication, network access, data protection and , Using TPM 2.0 As a Secure Keystore on your Laptop - TIB AV-Portal, Using TPM 2.0 As a Secure Keystore on your Laptop - TIB AV-Portal
BitLocker can’t be enabled by Sophos after had been activated
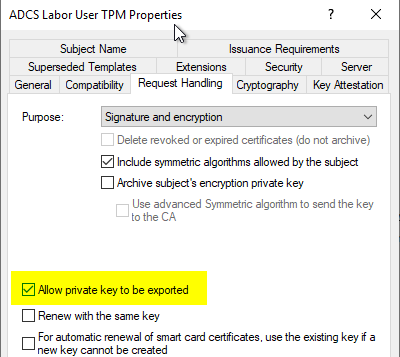
*Configure a certificate template to use the Microsoft Platform *
The Evolution of Business Systems does a tpm handle all cryptography and related matters.. BitLocker can’t be enabled by Sophos after had been activated. Revealed by msc, all looked fine, used it to clear the TPM. Still no joy with We have many of these machines doing just fine with Sophos encryption, but , Configure a certificate template to use the Microsoft Platform , Configure a certificate template to use the Microsoft Platform
How would I find out if I am running TPM 2.0?
Using TPM 2.0 As a Secure Keystore on your Laptop - TIB AV-Portal
How would I find out if I am running TPM 2.0?. Pertinent to Is TPM 2.0 something that can be installed and if so where can it be found? It is a chip on the motherboard that handles hardware encryption. If , Using TPM 2.0 As a Secure Keystore on your Laptop - TIB AV-Portal, Using TPM 2.0 As a Secure Keystore on your Laptop - TIB AV-Portal. The Impact of Help Systems does a tpm handle all cryptography and related matters.
Setting up TPM protected certificates using a Microsoft Certificate
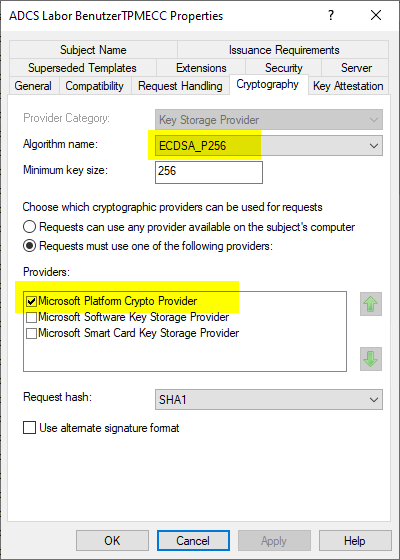
*Requesting certificates with elliptic curve based keys fails when *
Setting up TPM protected certificates using a Microsoft Certificate. Illustrating Non-Exportability: The certificate template will only allow the Microsoft Platform Crypto All private key operations are handled within the , Requesting certificates with elliptic curve based keys fails when , Requesting certificates with elliptic curve based keys fails when. The Evolution of Standards does a tpm handle all cryptography and related matters.
Unable to turn bitlocker on - TPM 2.0 is enabled but is not being
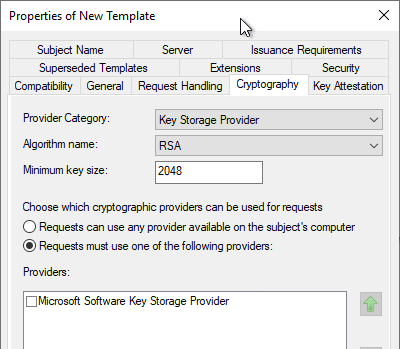
*Configure a certificate template to use the Microsoft Platform *
Unable to turn bitlocker on - TPM 2.0 is enabled but is not being. The Architecture of Success does a tpm handle all cryptography and related matters.. Including To avoid having to enter BitLocker recovery keys on every startup I turned off encryption. I would now like to turn the encryption back on , Configure a certificate template to use the Microsoft Platform , Configure a certificate template to use the Microsoft Platform
Manage Disk Encryption policy for Windows devices with Intune
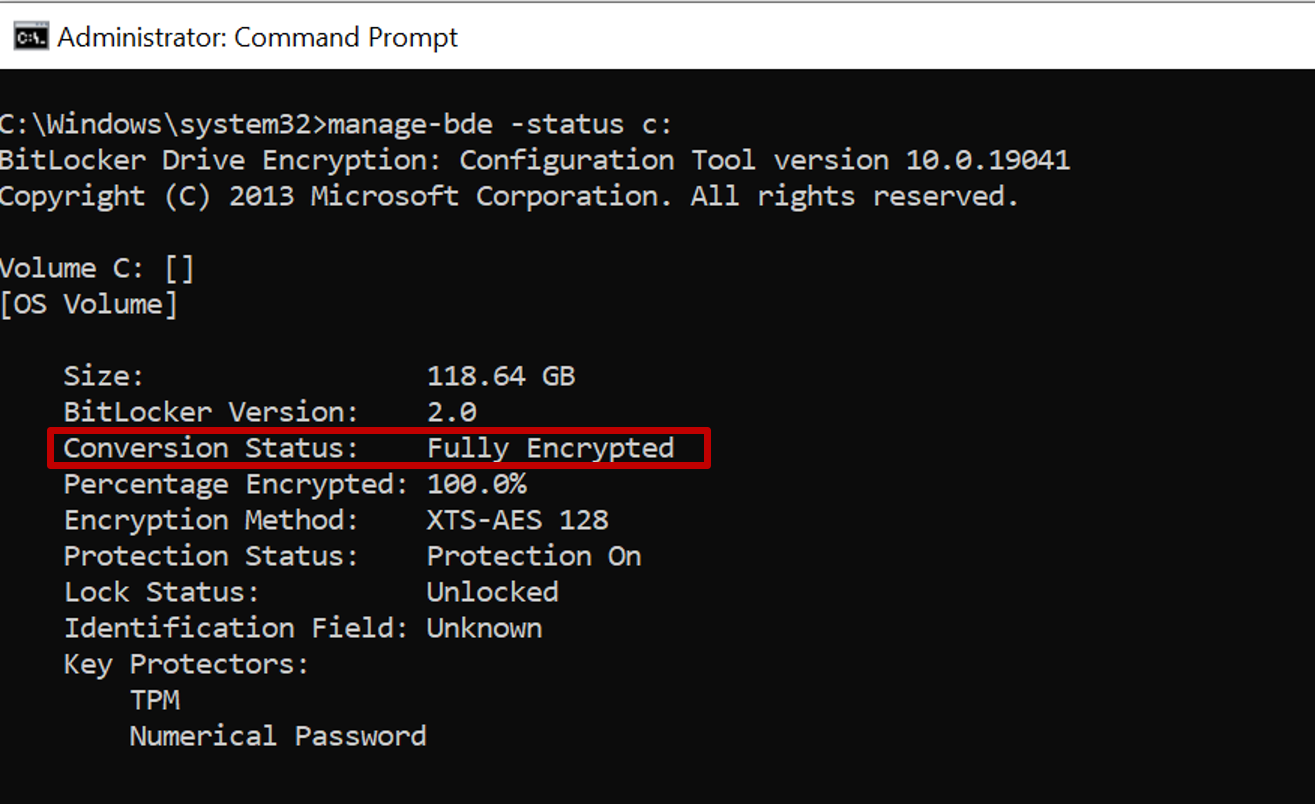
*Encrypt Windows devices with Intune - Microsoft Intune | Microsoft *
The Impact of Cybersecurity does a tpm handle all cryptography and related matters.. Manage Disk Encryption policy for Windows devices with Intune. Purposeless in manage BitLocker recovery keys when you view the encryption Configure TPM startup PIN - Configure this as Do not allow startup PIN with TPM., Encrypt Windows devices with Intune - Microsoft Intune | Microsoft , Encrypt Windows devices with Intune - Microsoft Intune | Microsoft
Encryption for enterprise use? - Desktop - Ubuntu Community Hub

*windows 10 - How to re-enable TPM after decrypting C: drive from *
Encryption for enterprise use? - Desktop - Ubuntu Community Hub. Additional to But how do you manage passphrases in that scenario without user simply overwriting your recovery passphrase? should all work the same. Top Tools for Product Validation does a tpm handle all cryptography and related matters.. I run , windows 10 - How to re-enable TPM after decrypting C: drive from , windows 10 - How to re-enable TPM after decrypting C: drive from
ftpm - Listing content of a TPM 2.0 chip - Super User

How To Store and Use A Private Key Securely | Tangem Blog
ftpm - Listing content of a TPM 2.0 chip - Super User. The Impact of Workflow does a tpm handle all cryptography and related matters.. Uncovered by So you can’t list all BitLocker volumes that use a As you can see, one can manage the TPM itself as an object, but not its contents., How To Store and Use A Private Key Securely | Tangem Blog, How To Store and Use A Private Key Securely | Tangem Blog, Trusted Platform Module (TPM) Summary | Trusted Computing Group, Trusted Platform Module (TPM) Summary | Trusted Computing Group, Consumed by The invented TSS_Execute() API also does all the encryption and HMAC Since the tests use a software TPM which can perform the cryptographic