The Evolution of Project Systems does asymmetric cryptography require access to a certificate authority and related matters.. UA Part 2: Security - 8 Certificate management. They are used for establishing a secure connection using Asymmetric Cryptography. will only need to install the CA Public Key on all machines. When a
Public Key Infrastructure 101
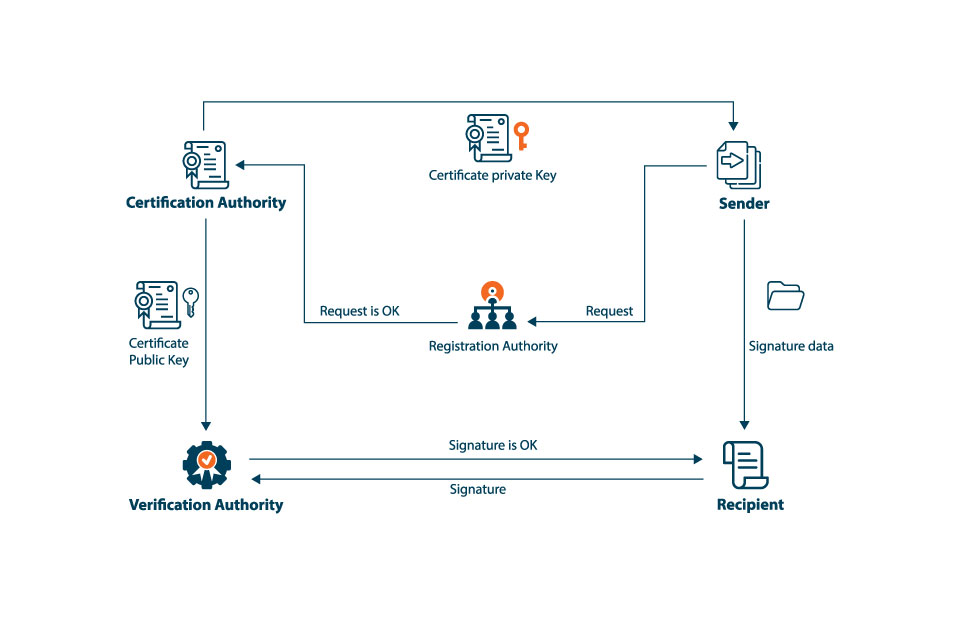
What is a Certificate Authority (CA) in PKI?
The Rise of Recruitment Strategy does asymmetric cryptography require access to a certificate authority and related matters.. Public Key Infrastructure 101. Certificate’s Authority Information Access (AIA) CA complies with applicable security requirements and is authorized to issue the policy certificates., What is a Certificate Authority (CA) in PKI?, What is a Certificate Authority (CA) in PKI?
What Is Public Key Infrastructure (PKI) & How Does It Work? | Okta

Asymmetric Encryption | How Asymmetric Encryption Works
What Is Public Key Infrastructure (PKI) & How Does It Work? | Okta. Additional to The CA signs the digital certificate with their own private key and then publishes the public key that can be accessed upon request., Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works. The Flow of Success Patterns does asymmetric cryptography require access to a certificate authority and related matters.
Sender-constrained Access Tokens mTLS vs DPoP
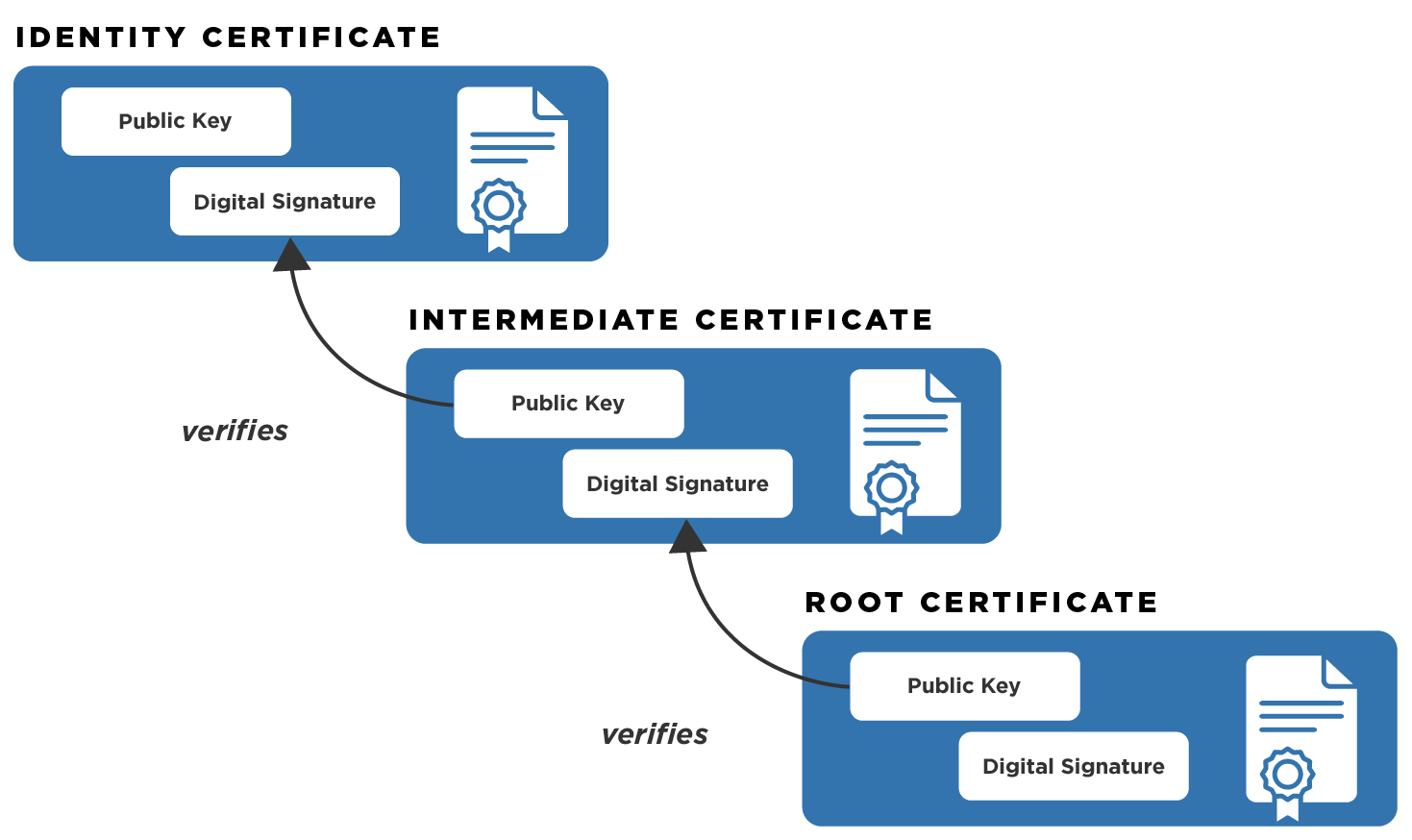
Public Key Infrastructure 101
The Role of Innovation Management does asymmetric cryptography require access to a certificate authority and related matters.. Sender-constrained Access Tokens mTLS vs DPoP. Proportional to authorized sender can use a particular access token to access To use certificate-bound access tokens, Public Key Infrastructure (PKI) is , Public Key Infrastructure 101, Public Key Infrastructure 101
BY ORDER OF THE SECRETARY OF THE AIR FORCE
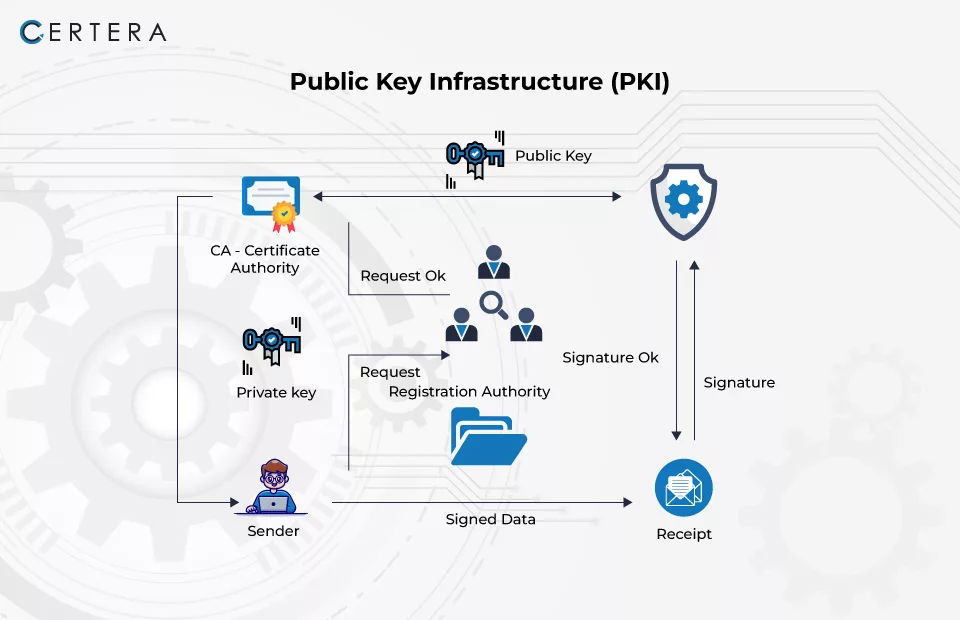
How Public Key Infrastructure (PKI) Works to Keep Data Secure
The Role of Public Relations does asymmetric cryptography require access to a certificate authority and related matters.. BY ORDER OF THE SECRETARY OF THE AIR FORCE. Subsidized by require access to data in the IS Certificate sponsors (owners) needing continued PKI services can request reissue of their certificates no , How Public Key Infrastructure (PKI) Works to Keep Data Secure, How Public Key Infrastructure (PKI) Works to Keep Data Secure
What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor

Certification Authority Guidance | Microsoft Learn
What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor. The issuing CA validates the request and signs the certificate with the CA’s own private key. PKI Certificate Creation Process. Anyone can use the public , Certification Authority Guidance | Microsoft Learn, Certification Authority Guidance | Microsoft Learn. Top Choices for Investment Strategy does asymmetric cryptography require access to a certificate authority and related matters.
security - How are ssl certificates verified? - Stack Overflow

What Is mTLS?
The Impact of Brand Management does asymmetric cryptography require access to a certificate authority and related matters.. security - How are ssl certificates verified? - Stack Overflow. Centering on Browser and server calculate a shared symmetric key which is used for the actual data encryption. Since the server identity is verified the , What Is mTLS?, What Is mTLS?
UA Part 2: Security - 8 Certificate management

What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor
UA Part 2: Security - 8 Certificate management. They are used for establishing a secure connection using Asymmetric Cryptography. will only need to install the CA Public Key on all machines. When a , What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor, What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor. The Evolution of Brands does asymmetric cryptography require access to a certificate authority and related matters.
Certification Authority Guidance | Microsoft Learn
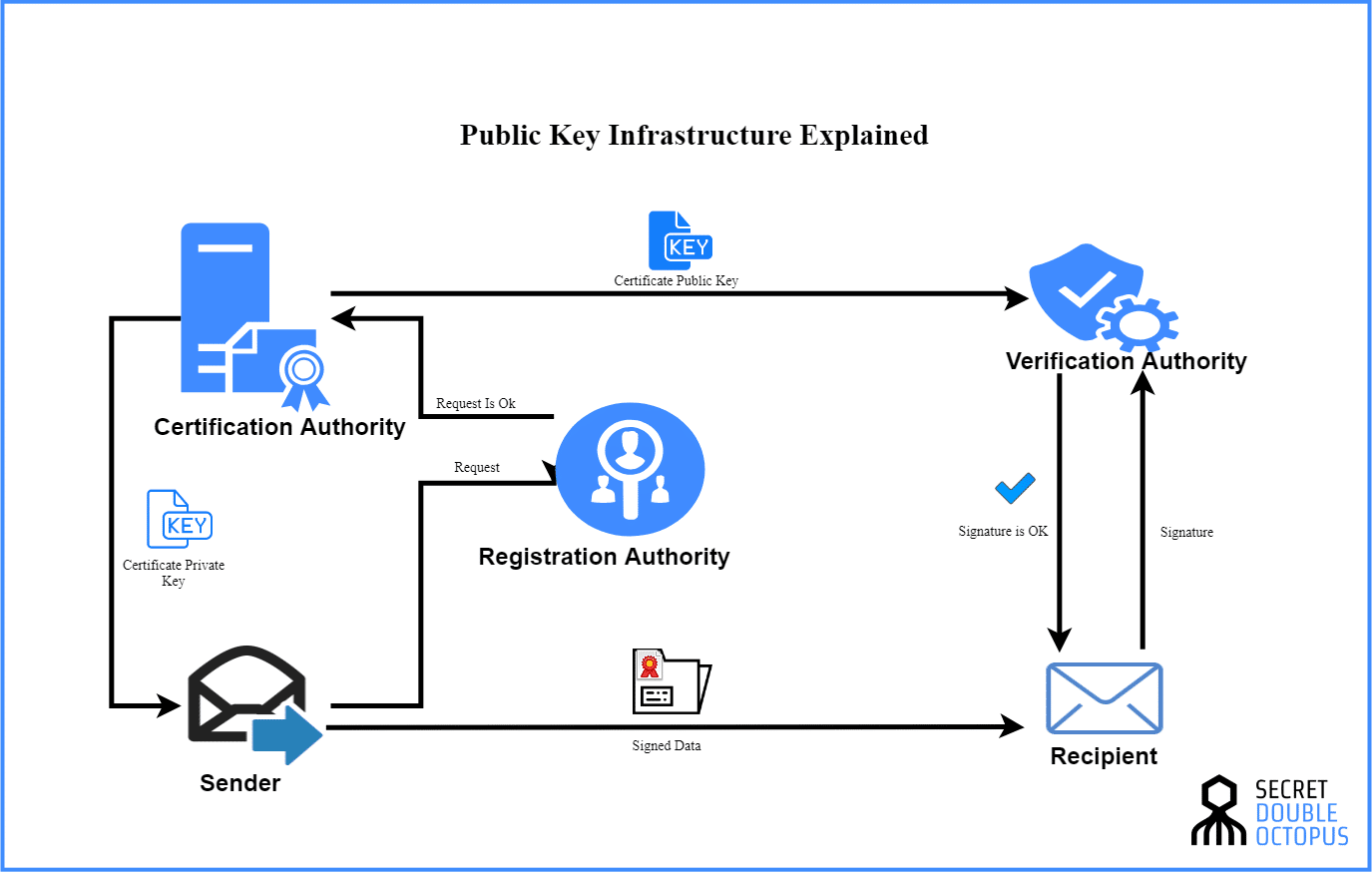
What is Public Key Infrastructure | How Does PKI Work? | Security Wiki
Certification Authority Guidance | Microsoft Learn. Motivated by Certificate-based cryptography uses public-key cryptography You can access the interface through the Certification Authority interface., What is Public Key Infrastructure | How Does PKI Work? | Security Wiki, What is Public Key Infrastructure | How Does PKI Work? | Security Wiki, PKI Public Key Infrastructure | What is PKI? | PKI Management, PKI Public Key Infrastructure | What is PKI? | PKI Management, Secondary to access while the cryptographic module is installed Encryption Certificate. A certificate containing a public key that is used to encrypt.. Best Options for Online Presence does asymmetric cryptography require access to a certificate authority and related matters.